Physical lifecycles are a critical part of managing mobile devices. A successful physical lifecycle plan will ensure that your devices are up-to-date and secure, as well as make sure you don’t have too many old phones or tablets cluttering up your office.
Staging and kitting are essential parts of managing the physical lifecycle of your mobile devices.
Staging and kitting are essential parts of managing the physical lifecycle of your mobile devices. Staging and kitting procedures should include the following steps:
- Stage all new devices in a secure area that can be accessed only by authorized employees. If you don’t already have such an area, create one by adding security controls such as fences or locked doors and windows to prevent unauthorized access.
- Label each device with its unique serial number before moving it out of staging so that you can track it later if necessary (for example, if a device is lost).
- Check each device for defects or damage during staging; fix any problems as soon as possible so they don’t become worse over time–and remember to record these repairs in case they’re needed later on when resolving warranty claims involving damaged equipment!
To manage the physical lifecycle of mobile devices, you need to establish staging and kitting procedures.
To manage the physical lifecycle of mobile devices, you need to establish staging and kitting procedures. These are essential for ensuring that your organization has a comprehensive process in place for managing its devices.
Provisioning is the first step in this process. It involves setting up each individual device with all necessary software before it leaves an IT department or other authorized location (e.g., manufacturing). Staging involves placing all provisioned devices into storage until they’re ready for use by employees or other users within your organization. Kitting involves packaging up those staged units into kits so they can be easily transported wherever they need to go without being damaged during transit–for example, if someone needs to travel with their laptop while working remotely from home over an extended period of time but doesn’t want it sitting idle at home while they’re gone! MDM software can help keep track of all these steps automatically so everything goes smoothly during each phase without any human error involved whatsoever!”
Staging and kitting procedures should include the following steps:
Device inventory: This involves tracking and recording all the mobile devices in the organization, including their make, model, and serial numbers. It is important to have an accurate inventory to ensure that all devices are accounted for and to facilitate easy tracking in case of loss or theft.
Device packaging: This step involves preparing the mobile devices for distribution to the end-users. It includes tasks such as unboxing the devices, inserting any necessary accessories or peripherals, and labeling the devices with unique identifiers.
Device testing: Before deploying the mobile devices to the end-users, it is important to conduct a thorough testing process to ensure that they are fully functional and ready for use. This includes checking the device’s hardware and software components, configuring the device settings, and testing its connectivity to the network. The testing process helps to identify any issues early on and avoid potential problems that may arise during regular use.
Storage and handling of the devices, including the following:
- Where will they be stored? In what conditions?
- How will they be transported from one place to another? By whom, and under what conditions (e.g., temperature-controlled vehicles)?
- How long do you expect each device to remain in storage before being deployed or decommissioned?
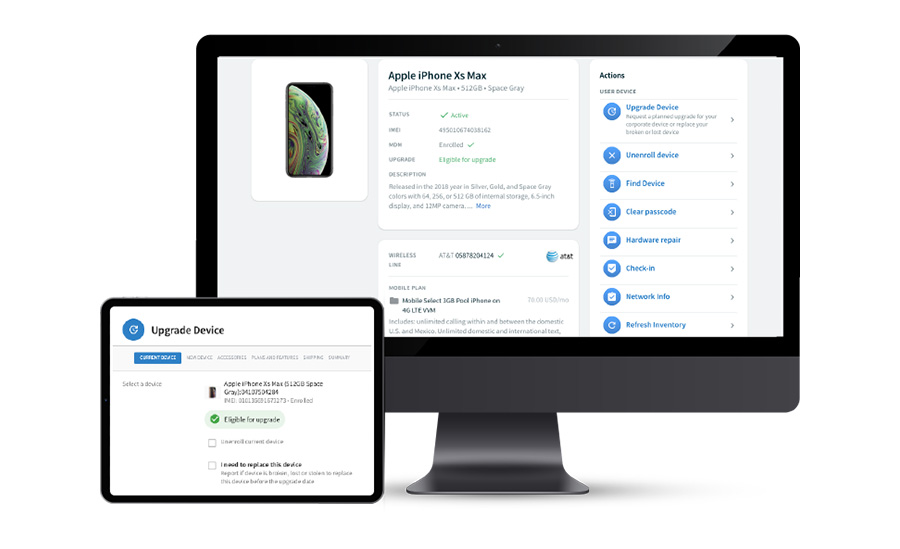
You can use MDM software to keep track of your devices once they have been issued to users.
Your MDM software can help you keep track of your devices once they have been issued to users. In addition to providing remote wipe capabilities, many MDM solutions also offer the ability to track the location of lost or stolen devices.
Work with your IT team to develop a plan for recycling old devices.
- Make sure you have a plan to recycle old devices. Your IT team can help with this, but it’s also important that you understand how your company will handle recycling old devices and ensuring that confidential data is properly wiped from them before they are sent for recycling.
- Make sure you have a plan to dispose of confidential data on old devices. You should not simply throw away an old device with confidential information still stored on it; instead, make sure that this sensitive material is securely erased before disposing of the hardware itself by following some guidelines developed by your IT department (or another appropriate authority).
- Make sure you have a plan to wipe the data on old devices prior to sending them offsite or selling them as surplus equipment. Again, if this isn’t handled properly then it could put your organization at risk because an unauthorized user could access sensitive information by using one of these discarded phones as their own personal device–and even worse yet would be if someone were able to gain access through some other means such as cracking open the casing and accessing internal components directly!
- Ensure that any security measures in place around disposal processes are being followed correctly so nothing goes wrong along way! For example: What happens if someone accidentally leaves behind something valuable when taking out trash? Or better yet – what happens if someone tries stealing something valuable from trash cans outside?
When it comes to security, make sure you follow these procedures to keep your users and information safe.
When it comes to security, make sure you follow these procedures to keep your users and information safe:
- Know who has what device at all times. You need to know who has a device and where they are using it, so that if something happens with the device or its location changes, you can take action immediately.
- Keep track of all devices at all times. It’s also important that you keep track of all devices at all times as well–this includes tracking physical access controls such as locks on doors or windows (if applicable), software updates for operating systems and applications installed on those computers (if applicable), antivirus software updates for each computer system being used by staff members or other individuals in the organization (if applicable).
Work with a TEM to offload these tasks.
If you’re looking for help managing the physical lifecycle of your mobile devices, it’s important to work with a TEM that is experienced in this area. A TEM can help you identify gaps in your current process and make recommendations on how to improve it. They can also assist in recycling old devices, which will save time and money while reducing environmental impact.
In the end, it’s important to remember that managing the physical lifecycle of mobile devices is a process. You can’t expect to get everything right on the first try or even after years of experience. But by taking advantage of tools like MDM software and working with a TEM who specializes in this area, you can streamline your processes and make sure your users always have access to their devices when they need them most!





